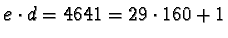Next: Some Observations
Up: EncryptionSeptember 30, 1997
Previous: Sharing a secret
- To receive encrypted messages a receiver must determine parameters e, d,
n.
- The receiver publishes e and n, it keeps d secret.
- Instead of sending plain text information P, transmitters compute the
remainder C when Pe is divided by n.
- The receiver recovers the unencrypted message P by computing the remainder
of Cd divided by n.
- This works only if d, e, n are chosen carefully.
- The following algorithm can be used to generate public key parameters d,
e, n.
- Algorithm:
- Select two prime numbers p and q.
- Let
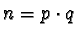 .
.
- Let
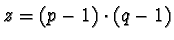 .
.
- Choose a number d that does not divide z.
- Choose a number e such that
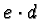 is a multiple of z plus 1.
is a multiple of z plus 1.
- Example:
- p=3, q=11
-
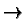 n=33, z=20
n=33, z=20
- Choose d=7
- Choose e=3,
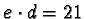 ,
i.e., z+1
,
i.e., z+1
- Example:
- p=11, q=17
-
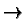 n=187, z=160
n=187, z=160
- Choose d=51
- Choose e=91,
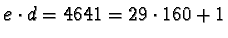
- The strength of this method for generating d, e, n is based on the fact
that is very difficult to find p and q from n if p and q are large
prime numbers.
Prof. Bernd-Peter Paris
1998-12-14
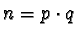 .
.
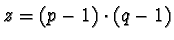 .
.
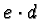 is a multiple of z plus 1.
is a multiple of z plus 1.
 n=33, z=20
n=33, z=20
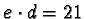 ,
i.e., z+1
,
i.e., z+1 n=187, z=160
n=187, z=160