


Next: Generating Random Numbers
Up: EncryptionSeptember 30, 1997
Previous: The Encryption Process
- To decrypt the encrypted message it must be xor'ed with the same random
sequence that was used for encryption.
| SYN |
NULL |
h |
N |
ETX |
a |
[ |
| 16x |
00x |
68x |
4Ex |
03x |
61x |
5Bx |
| 0010110 |
0000000 |
1101000 |
1001110 |
0000011 |
1100001 |
1011011 |
| |
|
|
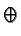 |
|
|
|
| 1010011 |
1000011 |
0101101 |
1101110 |
0110010 |
1010001 |
1101010 |
| |
|
|
= |
|
|
|
| 1000101 |
1000011 |
1000101 |
0100000 |
0110001 |
0110000 |
0110001 |
| 45x |
43x |
45x |
20x |
31x |
30x |
31x |
| E |
C |
E |
SPACE |
1 |
0 |
1 |
- Fundamentally, this works because
- Problems: How do we find the random sequence?
- How do transmitter and receiver agree on the same sequence?



Next: Generating Random Numbers
Up: EncryptionSeptember 30, 1997
Previous: The Encryption Process
Prof. Bernd-Peter Paris
1998-12-14
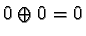 and
and
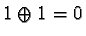
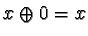 ,
for x=0 or x=1.
,
for x=0 or x=1.